The Key to secure your data in Cloud - AWS KMS

Cloud computing has allowed companies to reduce costs and boost operational efficiency, but it has also raised severe security implications leveraging public cloud platforms as part of their enterprise IT strategy.
If you are a data custodian or an IT admin, encrypting data should be your first line of defense, and managing the encryption keys is one of your primary concerns. Here are common challenges you encounter while designing and architecting an encryption key platform.
- How to generate the encryption keys?
- Encrypted data is safe only if the key is strong enough. If you use a weak key generation mechanism, someone can guess the keys, so the key generation process needs to use a cryptographically secure random generator.
- Where to store the encryption keys?
- You need secure, durable, and highly available storage to protect your keys.
- How to control access to the encryption keys?
- Access to the encryption keys should be based on the least privilege principle. It means users and applications should only have the necessary privileges to complete their tasks.
In AWS World, AWS Key Management Service (KMS) ticks all the boxes. AWS KMS is one powerful tool for your cloud security strategy. It gives you centralized control over the cryptographic keys to protect your data. The service is integrated with other AWS services making it easy to encrypt data you store in these services and control access to the keys that decrypt it.
This blog post will look at AWS Key management Service (KMS) concepts and features.
Concept of Envelope Encryption
AWS KMS uses the Envelope Encryption process; Envelope encryption is the practice of encrypting plaintext data with a data key, and then encrypting the data key with another key (known as root or master key).
Explanation with an example. Here, the plain text data is encrypted using a data key, and the data key itself is encrypted using another key commonly referred to as the root key. And then, the encrypted data key is stored along with the encrypted text data.
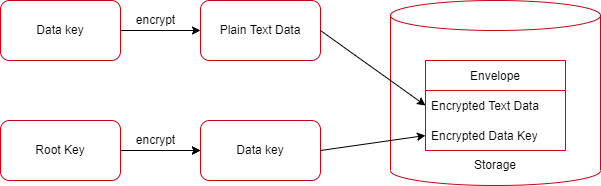
AWS KMS helps you protect your root encryption keys by storing and managing them securely. Root keys stored in AWS KMS are known as AWS KMS keys.
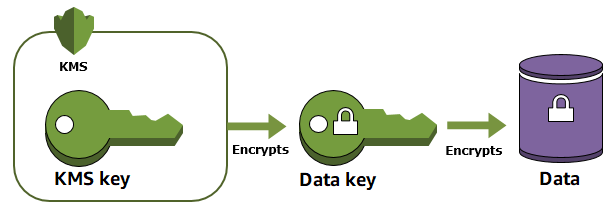
Types of KMS keys
There are 3 types of Root keys in AWS KMS.
- AWS Owned Keys
- AWS owned keys are a collection of KMS keys that an AWS service owns and manages for use in multiple AWS accounts. Although AWS owned keys are not in your AWS account, an AWS service can use the associated AWS owned keys to protect the resources in your account.
- AWS Managed Keys
- The AWS managed keys are KMS keys in your account created, managed, and used on your behalf by an AWS service integrated with AWS KMS
- Customer Managed Keys
- The Customer managed keys are KMS keys in your AWS account that you create, own, and manage. You have complete control over these KMS keys, including establishing and maintaining their key policies, IAM policies, and grants, enabling and disabling them, rotating their cryptographic material, adding tags, creating aliases that refer to the KMS keys, and scheduling the KMS keys for deletion.
- CMKs can be further broken down into two general types AWS-managed and customer-managed. To learn about AWS managed and customer managed CMKs.
Read more about KMS keys concepts.
Benefits of AWS KMS
- Fully managed – AWS KMS is a fully managed service to provide absolute scalability, durability, and high availability. It enables you to manage thousands of KMS keys, store multiple encrypted versions, and is designed for 99.999999999% durability.
- Secure – AWS KMS never leaves the AWS infrastructure and is designed so that no one can retrieve your plaintext keys. KMS uses a hardware security module (HSMs) that have been validated under FIPS 140-2.
- Compliance – AWS KMS is validated and certified by AWS Service Control Controls (SOC 1, SOC 2, and SOC 3) reports, PCI DSS Level 1, FIPS 140-2, FedRAMP, and HIPAA. Here is a list of other compliance regimes that AWS KMS is validated and certified against.
- Built-in Auditing – AWS KMS publishes all the events to AWS Cloudtrail Service. Each request you make to the AWS KMS service is logged and can be used for auditing purposes.
- Low Cost – Like all other AWS services, there is no upfront cost or commitment to use AWS KMS.
Conclusion
AWS KMS is a complete solution to manage cryptographic keys used across AWS services. Its native integration with other AWS services makes it easier for AWS KMS to encrypt the data you store and process.
By correctly architecting and implementing AWS KMS, you can guarantee that your encryption keys are protected and available for the application workloads and authorized identities. Additionally, AWS KMS publishes all the events to the AWS Cloudtrail service, enabling auditing and security monitoring of your key usage.